2014-02-17 15:54:25 +00:00
|
|
|
kpatch: dynamic kernel patching
|
|
|
|
|
===============================
|
2014-02-11 20:34:19 +00:00
|
|
|
|
2014-05-01 17:15:30 +00:00
|
|
|
kpatch is a Linux dynamic kernel patching infrastructure which allows you to
|
|
|
|
|
patch a running kernel without rebooting or restarting any processes. It
|
|
|
|
|
enables sysadmins to apply critical security patches to the kernel immediately,
|
|
|
|
|
without having to wait for long-running tasks to complete, for users to log
|
|
|
|
|
off, or for scheduled reboot windows. It gives more control over uptime
|
|
|
|
|
without sacrificing security or stability.
|
2014-02-11 20:34:19 +00:00
|
|
|
|
2014-02-18 23:33:20 +00:00
|
|
|
**WARNING: Use with caution! Kernel crashes, spontaneous reboots, and data loss
|
|
|
|
|
may occur!**
|
|
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
Here's a video of kpatch in action:
|
|
|
|
|
|
|
|
|
|
[](http://www.youtube.com/watch?v=juyQ5TsJRTA)
|
|
|
|
|
|
2014-07-11 14:53:23 +00:00
|
|
|
And a few more:
|
|
|
|
|
|
|
|
|
|
- https://www.youtube.com/watch?v=rN0sFjrJQfU
|
|
|
|
|
- https://www.youtube.com/watch?v=Mftc80KyjA4
|
|
|
|
|
|
2014-02-17 15:54:25 +00:00
|
|
|
Installation
|
|
|
|
|
------------
|
2014-02-13 16:04:35 +00:00
|
|
|
|
2017-04-18 03:23:37 +00:00
|
|
|
### Prerequisites
|
2014-04-29 18:33:02 +00:00
|
|
|
|
2017-04-18 03:23:37 +00:00
|
|
|
#### Fedora
|
2015-11-26 12:59:55 +00:00
|
|
|
|
|
|
|
|
*NOTE: You'll need about 15GB of free disk space for the kpatch-build cache in
|
|
|
|
|
`~/.kpatch` and for ccache.*
|
|
|
|
|
|
|
|
|
|
Install the dependencies for compiling kpatch:
|
|
|
|
|
|
|
|
|
|
```bash
|
2017-03-10 19:33:18 +00:00
|
|
|
UNAME=$(uname -r)
|
|
|
|
|
sudo dnf install gcc kernel-devel-${UNAME%.*} elfutils elfutils-devel
|
2015-11-26 12:59:55 +00:00
|
|
|
```
|
|
|
|
|
|
|
|
|
|
Install the dependencies for the "kpatch-build" command:
|
|
|
|
|
|
|
|
|
|
```bash
|
|
|
|
|
sudo dnf install rpmdevtools pesign yum-utils openssl wget numactl-devel
|
2017-03-10 19:33:18 +00:00
|
|
|
sudo dnf builddep kernel-${UNAME%.*}
|
|
|
|
|
sudo dnf debuginfo-install kernel-${UNAME%.*}
|
2015-11-26 12:59:55 +00:00
|
|
|
|
|
|
|
|
# optional, but highly recommended
|
|
|
|
|
sudo dnf install ccache
|
|
|
|
|
ccache --max-size=5G
|
2017-03-10 19:33:18 +00:00
|
|
|
|
|
|
|
|
# optional, for kpatch-test
|
|
|
|
|
sudo dnf install patchutils
|
2015-11-26 12:59:55 +00:00
|
|
|
```
|
|
|
|
|
|
2017-04-18 03:23:37 +00:00
|
|
|
#### RHEL 7
|
2014-07-15 17:06:32 +00:00
|
|
|
|
|
|
|
|
*NOTE: You'll need about 15GB of free disk space for the kpatch-build cache in
|
|
|
|
|
`~/.kpatch` and for ccache.*
|
|
|
|
|
|
|
|
|
|
Install the dependencies for compiling kpatch:
|
|
|
|
|
|
2014-07-25 12:59:01 +00:00
|
|
|
```bash
|
2017-03-10 19:33:18 +00:00
|
|
|
UNAME=$(uname -r)
|
|
|
|
|
sudo yum install gcc kernel-devel-${UNAME%.*} elfutils elfutils-devel
|
2014-07-25 12:59:01 +00:00
|
|
|
```
|
2014-07-15 17:06:32 +00:00
|
|
|
|
|
|
|
|
Install the dependencies for the "kpatch-build" command:
|
|
|
|
|
|
2014-07-25 12:59:01 +00:00
|
|
|
```bash
|
2014-09-30 02:20:35 +00:00
|
|
|
sudo yum-config-manager --enable rhel-7-server-optional-rpms
|
2014-07-25 12:59:01 +00:00
|
|
|
sudo yum install rpmdevtools pesign yum-utils zlib-devel \
|
|
|
|
|
binutils-devel newt-devel python-devel perl-ExtUtils-Embed \
|
2014-12-18 20:55:16 +00:00
|
|
|
audit-libs-devel numactl-devel pciutils-devel bison ncurses-devel
|
2014-07-25 12:59:01 +00:00
|
|
|
|
2017-03-10 19:33:18 +00:00
|
|
|
sudo yum-builddep kernel-${UNAME%.*}
|
|
|
|
|
sudo debuginfo-install kernel-${UNAME%.*}
|
2014-07-15 17:06:32 +00:00
|
|
|
|
2014-07-25 12:59:01 +00:00
|
|
|
# optional, but highly recommended
|
2017-03-10 19:33:18 +00:00
|
|
|
sudo yum install https://dl.fedoraproject.org/pub/epel/7/x86_64/c/ccache-3.2.7-3.el7.x86_64.rpm
|
2014-07-25 12:59:01 +00:00
|
|
|
ccache --max-size=5G
|
2017-03-10 19:33:18 +00:00
|
|
|
|
|
|
|
|
# optional, for kpatch-test
|
|
|
|
|
sudo dnf install patchutils
|
2014-07-25 12:59:01 +00:00
|
|
|
```
|
2014-07-15 17:06:32 +00:00
|
|
|
|
2017-04-18 03:23:37 +00:00
|
|
|
#### CentOS 7
|
2014-08-19 10:56:02 +00:00
|
|
|
|
|
|
|
|
*NOTE: You'll need about 15GB of free disk space for the kpatch-build cache in
|
|
|
|
|
`~/.kpatch` and for ccache.*
|
|
|
|
|
|
|
|
|
|
Install the dependencies for compiling kpatch:
|
|
|
|
|
|
|
|
|
|
```bash
|
2017-03-10 19:33:18 +00:00
|
|
|
UNAME=$(uname -r)
|
|
|
|
|
sudo yum install gcc kernel-devel-${UNAME%.*} elfutils elfutils-devel
|
2014-08-19 10:56:02 +00:00
|
|
|
```
|
|
|
|
|
|
|
|
|
|
Install the dependencies for the "kpatch-build" command:
|
|
|
|
|
|
|
|
|
|
```bash
|
|
|
|
|
sudo yum install rpmdevtools pesign yum-utils zlib-devel \
|
|
|
|
|
binutils-devel newt-devel python-devel perl-ExtUtils-Embed \
|
|
|
|
|
audit-libs audit-libs-devel numactl-devel pciutils-devel bison
|
|
|
|
|
|
|
|
|
|
# enable CentOS 7 debug repo
|
|
|
|
|
sudo yum-config-manager --enable debug
|
|
|
|
|
|
2017-03-10 19:33:18 +00:00
|
|
|
sudo yum-builddep kernel-${UNAME%.*}
|
|
|
|
|
sudo debuginfo-install kernel-${UNAME%.*}
|
2014-08-19 10:56:02 +00:00
|
|
|
|
|
|
|
|
# optional, but highly recommended - enable EPEL 7
|
|
|
|
|
sudo yum install ccache
|
|
|
|
|
ccache --max-size=5G
|
2017-03-10 19:33:18 +00:00
|
|
|
|
|
|
|
|
# optional, for kpatch-test
|
|
|
|
|
sudo dnf install patchutils
|
2014-08-19 10:56:02 +00:00
|
|
|
```
|
|
|
|
|
|
2017-04-18 03:23:37 +00:00
|
|
|
#### Oracle Linux 7
|
2014-08-19 10:56:02 +00:00
|
|
|
|
|
|
|
|
*NOTE: You'll need about 15GB of free disk space for the kpatch-build cache in
|
|
|
|
|
`~/.kpatch` and for ccache.*
|
|
|
|
|
|
|
|
|
|
Install the dependencies for compiling kpatch:
|
|
|
|
|
|
|
|
|
|
```bash
|
2017-03-10 19:33:18 +00:00
|
|
|
UNAME=$(uname -r)
|
|
|
|
|
sudo yum install gcc kernel-devel-${UNAME%.*} elfutils elfutils-devel
|
2014-08-19 10:56:02 +00:00
|
|
|
```
|
|
|
|
|
|
|
|
|
|
Install the dependencies for the "kpatch-build" command:
|
|
|
|
|
|
|
|
|
|
```bash
|
|
|
|
|
sudo yum install rpmdevtools pesign yum-utils zlib-devel \
|
|
|
|
|
binutils-devel newt-devel python-devel perl-ExtUtils-Embed \
|
|
|
|
|
audit-libs numactl-devel pciutils-devel bison
|
|
|
|
|
|
|
|
|
|
# enable ol7_optional_latest repo
|
|
|
|
|
sudo yum-config-manager --enable ol7_optional_latest
|
|
|
|
|
|
2017-03-10 19:33:18 +00:00
|
|
|
sudo yum-builddep kernel-${UNAME%.*}
|
2014-08-19 10:56:02 +00:00
|
|
|
|
|
|
|
|
# manually install kernel debuginfo packages
|
|
|
|
|
rpm -ivh https://oss.oracle.com/ol7/debuginfo/kernel-debuginfo-$(uname -r).rpm
|
|
|
|
|
rpm -ivh https://oss.oracle.com/ol7/debuginfo/kernel-debuginfo-common-x86_64-$(uname -r).rpm
|
|
|
|
|
|
|
|
|
|
# optional, but highly recommended - enable EPEL 7
|
|
|
|
|
sudo yum install ccache
|
|
|
|
|
ccache --max-size=5G
|
2017-03-10 19:33:18 +00:00
|
|
|
|
|
|
|
|
# optional, for kpatch-test
|
|
|
|
|
sudo dnf install patchutils
|
2014-08-19 10:56:02 +00:00
|
|
|
```
|
|
|
|
|
|
2017-04-18 03:23:37 +00:00
|
|
|
#### Ubuntu 14.04
|
2014-04-29 18:33:02 +00:00
|
|
|
|
2014-07-30 10:08:17 +00:00
|
|
|
*NOTE: You'll need about 15GB of free disk space for the kpatch-build cache in
|
|
|
|
|
`~/.kpatch` and for ccache.*
|
2014-06-13 22:29:29 +00:00
|
|
|
|
2014-04-29 18:33:02 +00:00
|
|
|
Install the dependencies for compiling kpatch:
|
|
|
|
|
|
2014-07-25 12:59:01 +00:00
|
|
|
```bash
|
|
|
|
|
apt-get install make gcc libelf-dev
|
|
|
|
|
```
|
2014-04-29 18:33:02 +00:00
|
|
|
|
|
|
|
|
Install the dependencies for the "kpatch-build" command:
|
|
|
|
|
|
2014-07-25 12:59:01 +00:00
|
|
|
```bash
|
2017-05-15 11:24:33 +00:00
|
|
|
apt-get install dpkg-dev devscripts
|
2014-07-25 12:59:01 +00:00
|
|
|
apt-get build-dep linux
|
2014-04-29 18:33:02 +00:00
|
|
|
|
2014-07-25 12:59:01 +00:00
|
|
|
# optional, but highly recommended
|
|
|
|
|
apt-get install ccache
|
|
|
|
|
ccache --max-size=5G
|
|
|
|
|
```
|
2014-04-29 18:33:02 +00:00
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
Install kernel debug symbols:
|
2014-05-23 13:39:03 +00:00
|
|
|
|
|
|
|
|
```bash
|
|
|
|
|
# Add ddebs repository
|
|
|
|
|
codename=$(lsb_release -sc)
|
|
|
|
|
sudo tee /etc/apt/sources.list.d/ddebs.list << EOF
|
|
|
|
|
deb http://ddebs.ubuntu.com/ ${codename} main restricted universe multiverse
|
|
|
|
|
deb http://ddebs.ubuntu.com/ ${codename}-security main restricted universe multiverse
|
|
|
|
|
deb http://ddebs.ubuntu.com/ ${codename}-updates main restricted universe multiverse
|
|
|
|
|
deb http://ddebs.ubuntu.com/ ${codename}-proposed main restricted universe multiverse
|
|
|
|
|
EOF
|
|
|
|
|
|
|
|
|
|
# add APT key
|
|
|
|
|
wget -Nq http://ddebs.ubuntu.com/dbgsym-release-key.asc -O- | sudo apt-key add -
|
|
|
|
|
apt-get update && apt-get install linux-image-$(uname -r)-dbgsym
|
|
|
|
|
```
|
2017-06-09 20:52:35 +00:00
|
|
|
If there are no packages published yet to the codename-security pocket, the
|
|
|
|
|
apt update may report a "404 Not Found" error, as well as a complaint about
|
|
|
|
|
disabling the repository by default. This message may be ignored (see issue
|
|
|
|
|
#710).
|
2014-05-23 13:39:03 +00:00
|
|
|
|
2017-04-18 03:23:37 +00:00
|
|
|
#### Debian 8.0
|
2014-07-08 17:21:47 +00:00
|
|
|
|
|
|
|
|
*NOTE: You'll need about 15GB of free disk space for the kpatch-build cache in
|
|
|
|
|
`~/.kpatch` and for ccache.*
|
|
|
|
|
|
|
|
|
|
Install the dependencies for compiling kpatch:
|
|
|
|
|
|
2014-07-08 17:25:29 +00:00
|
|
|
apt-get install make gcc libelf-dev build-essential
|
2014-07-08 17:21:47 +00:00
|
|
|
|
|
|
|
|
Install and prepare the kernel sources:
|
|
|
|
|
|
2014-07-21 02:53:50 +00:00
|
|
|
```bash
|
|
|
|
|
apt-get install linux-source-$(uname -r)
|
|
|
|
|
cd /usr/src && tar xvf linux-source-$(uname -r).tar.xz && ln -s linux-source-$(uname -r) linux && cd linux
|
|
|
|
|
cp /boot/config-$(uname -r) .config
|
|
|
|
|
for OPTION in CONFIG_KALLSYMS_ALL CONFIG_FUNCTION_TRACER ; do sed -i "s/# $OPTION is not set/$OPTION=y/g" .config ; done
|
|
|
|
|
sed -i "s/^SUBLEVEL.*/SUBLEVEL =/" Makefile
|
|
|
|
|
make -j`getconf _NPROCESSORS_CONF` deb-pkg KDEB_PKGVERSION=$(uname -r).9-1
|
|
|
|
|
```
|
2014-07-08 17:21:47 +00:00
|
|
|
|
|
|
|
|
Install the kernel packages and reboot
|
|
|
|
|
|
|
|
|
|
dpkg -i /usr/src/*.deb
|
|
|
|
|
reboot
|
|
|
|
|
|
|
|
|
|
Install the dependencies for the "kpatch-build" command:
|
|
|
|
|
|
|
|
|
|
apt-get install dpkg-dev
|
|
|
|
|
apt-get build-dep linux
|
|
|
|
|
|
|
|
|
|
# optional, but highly recommended
|
|
|
|
|
apt-get install ccache
|
|
|
|
|
ccache --max-size=5G
|
|
|
|
|
|
2017-04-18 03:23:37 +00:00
|
|
|
#### Debian 7.x
|
2014-07-21 02:53:50 +00:00
|
|
|
|
|
|
|
|
*NOTE: You'll need about 15GB of free disk space for the kpatch-build cache in
|
|
|
|
|
`~/.kpatch` and for ccache.*
|
|
|
|
|
|
|
|
|
|
Add backports repositories:
|
|
|
|
|
|
|
|
|
|
```bash
|
|
|
|
|
echo "deb http://http.debian.net/debian wheezy-backports main" > /etc/apt/sources.list.d/wheezy-backports.list
|
|
|
|
|
echo "deb http://packages.incloudus.com backports-incloudus main" > /etc/apt/sources.list.d/incloudus.list
|
|
|
|
|
wget http://packages.incloudus.com/incloudus/incloudus.pub -O- | apt-key add -
|
|
|
|
|
aptitude update
|
|
|
|
|
```
|
|
|
|
|
|
|
|
|
|
Install the linux kernel, symbols and gcc 4.9:
|
|
|
|
|
|
|
|
|
|
aptitude install -t wheezy-backports -y initramfs-tools
|
2014-07-30 17:51:45 +00:00
|
|
|
aptitude install -y gcc gcc-4.9 g++-4.9 linux-image-3.14 linux-image-3.14-dbg
|
2014-07-21 02:53:50 +00:00
|
|
|
|
|
|
|
|
Configure gcc 4.9 as the default gcc compiler:
|
|
|
|
|
|
|
|
|
|
update-alternatives --install /usr/bin/gcc gcc /usr/bin/gcc-4.7 20
|
|
|
|
|
update-alternatives --install /usr/bin/gcc gcc /usr/bin/gcc-4.9 50
|
|
|
|
|
update-alternatives --install /usr/bin/g++ g++ /usr/bin/g++-4.7 20
|
|
|
|
|
update-alternatives --install /usr/bin/g++ g++ /usr/bin/g++-4.9 50
|
|
|
|
|
|
|
|
|
|
Install kpatch and these dependencies:
|
|
|
|
|
|
|
|
|
|
aptitude install kpatch
|
|
|
|
|
|
|
|
|
|
Configure ccache (installed by kpatch package):
|
|
|
|
|
|
|
|
|
|
ccache --max-size=5G
|
|
|
|
|
|
|
|
|
|
|
2017-04-18 03:23:37 +00:00
|
|
|
### Build
|
2014-04-29 18:33:02 +00:00
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
Compile kpatch:
|
2014-02-13 16:04:35 +00:00
|
|
|
|
|
|
|
|
make
|
2014-02-18 16:15:13 +00:00
|
|
|
|
2017-04-18 03:23:37 +00:00
|
|
|
### Install
|
2014-04-29 18:33:02 +00:00
|
|
|
|
2014-07-25 12:59:01 +00:00
|
|
|
OPTIONAL: Install kpatch to `/usr/local`:
|
2014-02-18 16:15:13 +00:00
|
|
|
|
2014-02-13 16:04:35 +00:00
|
|
|
sudo make install
|
|
|
|
|
|
2014-07-30 10:08:17 +00:00
|
|
|
Alternatively, the kpatch and kpatch-build scripts can be run directly from the
|
|
|
|
|
git tree.
|
2014-04-22 02:43:57 +00:00
|
|
|
|
2014-02-13 16:04:35 +00:00
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
Quick start
|
2014-02-17 15:54:25 +00:00
|
|
|
-----------
|
2014-02-13 03:53:05 +00:00
|
|
|
|
2014-07-30 10:08:17 +00:00
|
|
|
> NOTE: While kpatch is designed to work with any recent Linux
|
|
|
|
|
kernel on any distribution, the `kpatch-build` command has **ONLY** been tested
|
2015-12-04 13:07:52 +00:00
|
|
|
and confirmed to work on Fedora 20 and later, RHEL 7, Oracle Linux 7, CentOS 7 and Ubuntu 14.04.
|
2014-02-13 03:53:05 +00:00
|
|
|
|
2014-05-02 22:28:58 +00:00
|
|
|
First, make a source code patch against the kernel tree using diff, git, or
|
|
|
|
|
quilt.
|
|
|
|
|
|
|
|
|
|
As a contrived example, let's patch /proc/meminfo to show VmallocChunk in ALL
|
|
|
|
|
CAPS so we can see it better:
|
|
|
|
|
|
|
|
|
|
$ cat meminfo-string.patch
|
|
|
|
|
Index: src/fs/proc/meminfo.c
|
|
|
|
|
===================================================================
|
|
|
|
|
--- src.orig/fs/proc/meminfo.c
|
|
|
|
|
+++ src/fs/proc/meminfo.c
|
|
|
|
|
@@ -95,7 +95,7 @@ static int meminfo_proc_show(struct seq_
|
|
|
|
|
"Committed_AS: %8lu kB\n"
|
|
|
|
|
"VmallocTotal: %8lu kB\n"
|
|
|
|
|
"VmallocUsed: %8lu kB\n"
|
|
|
|
|
- "VmallocChunk: %8lu kB\n"
|
|
|
|
|
+ "VMALLOCCHUNK: %8lu kB\n"
|
|
|
|
|
#ifdef CONFIG_MEMORY_FAILURE
|
|
|
|
|
"HardwareCorrupted: %5lu kB\n"
|
|
|
|
|
#endif
|
2014-02-18 04:37:07 +00:00
|
|
|
|
2014-04-01 21:40:28 +00:00
|
|
|
Build the patch module:
|
2014-02-18 04:37:07 +00:00
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
$ kpatch-build -t vmlinux meminfo-string.patch
|
2014-05-02 22:28:58 +00:00
|
|
|
Using cache at /home/jpoimboe/.kpatch/3.13.10-200.fc20.x86_64/src
|
|
|
|
|
Testing patch file
|
|
|
|
|
checking file fs/proc/meminfo.c
|
|
|
|
|
Building original kernel
|
|
|
|
|
Building patched kernel
|
|
|
|
|
Detecting changed objects
|
|
|
|
|
Rebuilding changed objects
|
|
|
|
|
Extracting new and modified ELF sections
|
|
|
|
|
meminfo.o: changed function: meminfo_proc_show
|
|
|
|
|
Building patch module: kpatch-meminfo-string.ko
|
|
|
|
|
SUCCESS
|
|
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
> NOTE: The `-t vmlinux` option is used to tell `kpatch-build` to only look for
|
|
|
|
|
> changes in the `vmlinux` base kernel image, which is much faster than also
|
|
|
|
|
> compiling all the kernel modules. If your patch affects a kernel module, you
|
|
|
|
|
> can either omit this option to build everything, and have `kpatch-build`
|
|
|
|
|
> detect which modules changed, or you can specify the affected kernel build
|
|
|
|
|
> targets with multiple `-t` options.
|
|
|
|
|
|
2014-05-02 22:28:58 +00:00
|
|
|
That outputs a patch module named `kpatch-meminfo-string.ko` in the current
|
2014-02-18 04:37:07 +00:00
|
|
|
directory. Now apply it to the running kernel:
|
|
|
|
|
|
2014-05-02 22:28:58 +00:00
|
|
|
$ sudo kpatch load kpatch-meminfo-string.ko
|
|
|
|
|
loading core module: /usr/local/lib/modules/3.13.10-200.fc20.x86_64/kpatch/kpatch.ko
|
|
|
|
|
loading patch module: kpatch-meminfo-string.ko
|
2014-02-18 04:37:07 +00:00
|
|
|
|
|
|
|
|
Done! The kernel is now patched.
|
2014-02-13 03:53:05 +00:00
|
|
|
|
2014-05-02 22:28:58 +00:00
|
|
|
$ grep -i chunk /proc/meminfo
|
|
|
|
|
VMALLOCCHUNK: 34359337092 kB
|
2014-02-13 16:04:35 +00:00
|
|
|
|
2015-11-16 20:59:41 +00:00
|
|
|
|
|
|
|
|
Patch Author Guide
|
|
|
|
|
------------------
|
|
|
|
|
|
|
|
|
|
Unfortunately, live patching isn't always as easy as the previous example, and
|
|
|
|
|
can have some major pitfalls if you're not careful. To learn more about how to
|
|
|
|
|
properly create live patches, see the [Patch Author
|
|
|
|
|
Guide](doc/patch-author-guide.md).
|
|
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
How it works
|
2014-02-17 15:54:25 +00:00
|
|
|
------------
|
2014-02-11 18:00:17 +00:00
|
|
|
|
2014-02-19 03:32:24 +00:00
|
|
|
kpatch works at a function granularity: old functions are replaced with new
|
|
|
|
|
ones. It has four main components:
|
|
|
|
|
|
|
|
|
|
- **kpatch-build**: a collection of tools which convert a source diff patch to
|
2014-04-01 21:40:28 +00:00
|
|
|
a patch module. They work by compiling the kernel both with and without
|
|
|
|
|
the source patch, comparing the binaries, and generating a patch module
|
2014-02-19 03:32:24 +00:00
|
|
|
which includes new binary versions of the functions to be replaced.
|
|
|
|
|
|
2014-04-01 21:40:28 +00:00
|
|
|
- **patch module**: a kernel module (.ko file) which includes the
|
2014-02-19 03:32:24 +00:00
|
|
|
replacement functions and metadata about the original functions.
|
|
|
|
|
|
|
|
|
|
- **kpatch core module**: a kernel module (.ko file) which provides an
|
2014-04-01 21:40:28 +00:00
|
|
|
interface for the patch modules to register new functions for
|
2014-02-19 03:32:24 +00:00
|
|
|
replacement. It uses the kernel ftrace subsystem to hook into the original
|
|
|
|
|
function's mcount call instruction, so that a call to the original function
|
|
|
|
|
is redirected to the replacement function.
|
|
|
|
|
|
|
|
|
|
- **kpatch utility:** a command-line tool which allows a user to manage a
|
2014-04-01 21:40:28 +00:00
|
|
|
collection of patch modules. One or more patch modules may be
|
2014-02-19 15:50:56 +00:00
|
|
|
configured to load at boot time, so that a system can remain patched
|
2014-02-19 03:32:24 +00:00
|
|
|
even after a reboot into the same version of the kernel.
|
|
|
|
|
|
|
|
|
|
|
2014-03-10 14:24:40 +00:00
|
|
|
### kpatch-build
|
2014-02-11 18:00:17 +00:00
|
|
|
|
2014-04-01 21:40:28 +00:00
|
|
|
The "kpatch-build" command converts a source-level diff patch file to a kernel
|
|
|
|
|
patch module. Most of its work is performed by the kpatch-build script
|
2014-06-16 04:32:08 +00:00
|
|
|
which uses a utility named `create-diff-object` to compare changed objects.
|
2014-02-11 18:00:17 +00:00
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
The primary steps in kpatch-build are:
|
|
|
|
|
- Build the unstripped vmlinux for the kernel
|
|
|
|
|
- Patch the source tree
|
|
|
|
|
- Rebuild vmlinux and monitor which objects are being rebuilt.
|
2014-02-11 18:00:17 +00:00
|
|
|
These are the "changed objects".
|
2014-02-18 16:15:13 +00:00
|
|
|
- Recompile each changed object with `-ffunction-sections -fdata-sections`,
|
2014-02-11 18:00:17 +00:00
|
|
|
resulting in the changed patched objects
|
|
|
|
|
- Unpatch the source tree
|
2014-02-18 16:15:13 +00:00
|
|
|
- Recompile each changed object with `-ffunction-sections -fdata-sections`,
|
2014-02-13 13:49:02 +00:00
|
|
|
resulting in the changed original objects
|
2014-06-16 04:32:08 +00:00
|
|
|
- For every changed object, use `create-diff-object` to do the following:
|
|
|
|
|
* Analyze each original/patched object pair for patchability
|
2014-06-18 19:41:31 +00:00
|
|
|
* Add `.kpatch.funcs` and `.rela.kpatch.funcs` sections to the output object.
|
2014-06-16 04:32:08 +00:00
|
|
|
The kpatch core module uses this to determine the list of functions
|
|
|
|
|
that need to be redirected using ftrace.
|
2014-06-16 04:40:48 +00:00
|
|
|
* Add `.kpatch.dynrelas` and `.rela.kpatch.dynrelas` sections to the output object.
|
2014-06-16 04:32:08 +00:00
|
|
|
This will be used to resolve references to non-included local
|
|
|
|
|
and non-exported global symbols. These relocations will be resolved by the kpatch core module.
|
|
|
|
|
* Generate the resulting output object containing the new and modified sections
|
2014-02-18 16:15:13 +00:00
|
|
|
- Link all the output objects into a cumulative object
|
2014-04-01 21:40:28 +00:00
|
|
|
- Generate the patch module
|
2014-02-11 20:34:19 +00:00
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
### Patching
|
|
|
|
|
|
2014-04-01 21:40:28 +00:00
|
|
|
The patch modules register with the core module (`kpatch.ko`).
|
2014-02-18 16:15:13 +00:00
|
|
|
They provide information about original functions that need to be replaced, and
|
|
|
|
|
corresponding function pointers to the replacement functions.
|
|
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
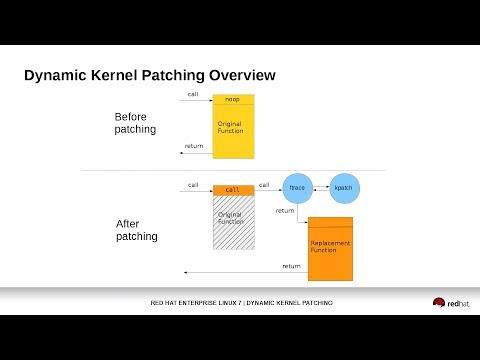
The core module registers a handler function with ftrace. The
|
|
|
|
|
handler function is called by ftrace immediately before the original
|
2014-02-18 16:15:13 +00:00
|
|
|
function begins executing. This occurs with the help of the reserved mcount
|
|
|
|
|
call at the beginning of every function, created by the gcc `-mfentry` flag.
|
2014-06-18 19:41:31 +00:00
|
|
|
The ftrace handler then modifies the return instruction pointer (IP)
|
2014-02-18 16:15:13 +00:00
|
|
|
address on the stack and returns to ftrace, which then restores the original
|
|
|
|
|
function's arguments and stack, and "returns" to the new function.
|
|
|
|
|
|
2014-02-11 20:34:19 +00:00
|
|
|
|
2014-02-18 23:33:20 +00:00
|
|
|
Limitations
|
|
|
|
|
-----------
|
|
|
|
|
|
2014-03-21 19:57:52 +00:00
|
|
|
- Patches which modify init functions (annotated with `__init`) are not
|
|
|
|
|
supported. kpatch-build will return an error if the patch attempts
|
|
|
|
|
to do so.
|
|
|
|
|
|
|
|
|
|
- Patches which modify statically allocated data are not supported.
|
|
|
|
|
kpatch-build will detect that and return an error. (In the future
|
|
|
|
|
we will add a facility to support it. It will probably require the
|
2014-04-01 21:40:28 +00:00
|
|
|
user to write code which runs at patch module loading time which manually
|
2014-03-21 19:57:52 +00:00
|
|
|
updates the data.)
|
|
|
|
|
|
|
|
|
|
- Patches which change the way a function interacts with dynamically
|
|
|
|
|
allocated data might be safe, or might not. It isn't possible for
|
|
|
|
|
kpatch-build to verify the safety of this kind of patch. It's up to
|
|
|
|
|
the user to understand what the patch does, whether the new functions
|
|
|
|
|
interact with dynamically allocated data in a different way than the
|
|
|
|
|
old functions did, and whether it would be safe to atomically apply
|
|
|
|
|
such a patch to a running kernel.
|
2014-02-18 23:33:20 +00:00
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
- Patches which modify functions in vdso are not supported. These run in
|
|
|
|
|
user-space and ftrace can't hook them.
|
|
|
|
|
|
2017-03-10 19:06:20 +00:00
|
|
|
- Patches which modify functions that are missing a `fentry` call are not
|
|
|
|
|
supported. This includes any `lib-y` targets that are archived into a
|
|
|
|
|
`lib.a` library for later linking (for example, `lib/string.o`).
|
|
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
- Some incompatibilities currently exist between kpatch and usage of ftrace and
|
|
|
|
|
kprobes. See the Frequently Asked Questions section for more details.
|
|
|
|
|
|
2014-02-18 23:33:20 +00:00
|
|
|
|
2014-02-19 21:49:15 +00:00
|
|
|
Frequently Asked Questions
|
|
|
|
|
--------------------------
|
|
|
|
|
|
2015-03-25 22:17:09 +00:00
|
|
|
**Q. What's the relationship between kpatch and the upstream Linux live kernel
|
|
|
|
|
patching component (livepatch)?**
|
|
|
|
|
|
2015-06-24 21:29:29 +00:00
|
|
|
Starting with Linux 4.0, the Linux kernel has livepatch, which is a new
|
2015-03-25 22:17:09 +00:00
|
|
|
converged live kernel patching framework. Livepatch is similar in
|
|
|
|
|
functionality to the kpatch core module, though it doesn't yet have all the
|
|
|
|
|
features that kpatch does.
|
|
|
|
|
|
|
|
|
|
kpatch-build already works with both livepatch and kpatch. If your kernel has
|
|
|
|
|
CONFIG\_LIVEPATCH enabled, it detects that and builds a patch module in the
|
|
|
|
|
livepatch format. Otherwise it builds a kpatch patch module.
|
|
|
|
|
|
2017-02-06 18:51:53 +00:00
|
|
|
The kpatch script also supports both patch module formats.
|
2015-03-25 22:17:09 +00:00
|
|
|
|
2014-02-19 21:49:15 +00:00
|
|
|
**Q. Isn't this just a virus/rootkit injection framework?**
|
|
|
|
|
|
|
|
|
|
kpatch uses kernel modules to replace code. It requires the `CAP_SYS_MODULE`
|
|
|
|
|
capability. If you already have that capability, then you already have the
|
|
|
|
|
ability to arbitrarily modify the kernel, with or without kpatch.
|
|
|
|
|
|
|
|
|
|
**Q. How can I detect if somebody has patched the kernel?**
|
|
|
|
|
|
2017-02-06 18:51:53 +00:00
|
|
|
When a patch module is loaded, the `TAINT_USER` or `TAINT_LIVEPATCH` flag is
|
|
|
|
|
set. (The latter flag was introduced in Linux version 4.0.) To test for
|
|
|
|
|
these flags, `cat /proc/sys/kernel/tainted` and check to see if the value of
|
|
|
|
|
`TAINT_USER` (64) or `TAINT_LIVEPATCH` (32768) has been OR'ed in.
|
2014-05-01 17:15:58 +00:00
|
|
|
|
2014-05-01 17:19:41 +00:00
|
|
|
Note that the `TAINT_OOT_MODULE` flag (4096) will also be set, since the patch
|
2014-05-01 17:15:58 +00:00
|
|
|
module is built outside the Linux kernel source tree.
|
|
|
|
|
|
|
|
|
|
If your patch module is unsigned, the `TAINT_FORCED_MODULE` flag (2) will also
|
|
|
|
|
be set. Starting with Linux 3.15, this will be changed to the more specific
|
|
|
|
|
`TAINT_UNSIGNED_MODULE` (8192).
|
2014-02-19 21:49:15 +00:00
|
|
|
|
2017-02-06 18:51:53 +00:00
|
|
|
Linux versions starting with 4.9 also support a per-module `TAINT_LIVEPATCH`
|
|
|
|
|
taint flag. This can be checked by verifying the output of
|
|
|
|
|
`cat /sys/module/<kpatch module>/taint` -- a 'K' character indicates the
|
|
|
|
|
presence of `TAINT_LIVEPATCH`.
|
|
|
|
|
|
2014-02-19 21:49:15 +00:00
|
|
|
**Q. Will it destabilize my system?**
|
|
|
|
|
|
|
|
|
|
No, as long as the patch is chosen carefully. See the Limitations section
|
|
|
|
|
above.
|
|
|
|
|
|
|
|
|
|
**Q. Why does kpatch use ftrace to jump to the replacement function instead of
|
|
|
|
|
adding the jump directly?**
|
|
|
|
|
|
|
|
|
|
ftrace owns the first "call mcount" instruction of every kernel function. In
|
|
|
|
|
order to keep compatibility with ftrace, we go through ftrace rather than
|
2014-06-18 19:41:31 +00:00
|
|
|
updating the instruction directly. This approach also ensures that the code
|
|
|
|
|
modification path is reliable, since ftrace has been doing it successfully for
|
|
|
|
|
years.
|
2014-02-19 21:49:15 +00:00
|
|
|
|
|
|
|
|
**Q Is kpatch compatible with \<insert kernel debugging subsystem here\>?**
|
|
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
We aim to be good kernel citizens and maintain compatibility. A kpatch
|
2014-02-19 21:49:15 +00:00
|
|
|
replacement function is no different than a function loaded by any other kernel
|
|
|
|
|
module. Each replacement function has its own symbol name and kallsyms entry,
|
|
|
|
|
so it looks like a normal function to the kernel.
|
|
|
|
|
|
|
|
|
|
- **oops stack traces**: Yes. If the replacement function is involved in an
|
|
|
|
|
oops, the stack trace will show the function and kernel module name of the
|
|
|
|
|
replacement function, just like any other kernel module function. The oops
|
2017-04-03 14:00:46 +00:00
|
|
|
message will also show the taint flag (see the FAQ "How can I detect if
|
|
|
|
|
somebody has patched the kernel" for specifics).
|
2014-02-19 21:49:15 +00:00
|
|
|
- **kdump/crash**: Yes. Replacement functions are normal functions, so crash
|
2014-06-18 19:41:31 +00:00
|
|
|
will have no issues.
|
|
|
|
|
- **ftrace**: Yes, but certain uses of ftrace which involve opening the
|
|
|
|
|
`/sys/kernel/debug/tracing/trace` file or using `trace-cmd record` can result
|
|
|
|
|
in a tiny window of time where a patch gets temporarily disabled. Therefore
|
|
|
|
|
it's a good idea to avoid using ftrace on a patched system until this issue
|
|
|
|
|
is resolved.
|
2014-04-23 19:22:58 +00:00
|
|
|
- **systemtap/kprobes**: Some incompatibilities exist.
|
|
|
|
|
- If you setup a kprobe module at the beginning of a function before loading
|
|
|
|
|
a kpatch module, and they both affect the same function, kprobes "wins"
|
|
|
|
|
until the kprobe has been unregistered. This is tracked in issue
|
|
|
|
|
[#47](https://github.com/dynup/kpatch/issues/47).
|
|
|
|
|
- Setting a kretprobe before loading a kpatch module could be unsafe. See
|
|
|
|
|
issue [#67](https://github.com/dynup/kpatch/issues/67).
|
2014-06-18 19:41:31 +00:00
|
|
|
- **perf**: Yes.
|
|
|
|
|
- **tracepoints**: Patches to a function which uses tracepoints will result in
|
|
|
|
|
the tracepoints being effectively disabled as long as the patch is applied.
|
2014-02-19 21:49:15 +00:00
|
|
|
|
|
|
|
|
**Q. Why not use something like kexec instead?**
|
|
|
|
|
|
|
|
|
|
If you want to avoid a hardware reboot, but are ok with restarting processes,
|
|
|
|
|
kexec is a good alternative.
|
|
|
|
|
|
|
|
|
|
**Q. If an application can't handle a reboot, it's designed wrong.**
|
|
|
|
|
|
|
|
|
|
That's a good poi... [system reboots]
|
|
|
|
|
|
|
|
|
|
**Q. What changes are needed in other upstream projects?**
|
|
|
|
|
|
|
|
|
|
We hope to make the following changes to other projects:
|
|
|
|
|
|
|
|
|
|
- kernel:
|
|
|
|
|
- ftrace improvements to close any windows that would allow a patch to
|
|
|
|
|
be inadvertently disabled
|
|
|
|
|
|
|
|
|
|
**Q: Is it possible to register a function that gets called atomically with
|
|
|
|
|
`stop_machine` when the patch module loads and unloads?**
|
|
|
|
|
|
|
|
|
|
We do have plans to implement something like that.
|
|
|
|
|
|
2014-02-21 03:10:09 +00:00
|
|
|
**Q. What kernels are supported?**
|
|
|
|
|
|
2014-07-15 16:38:20 +00:00
|
|
|
kpatch needs gcc >= 4.8 and Linux >= 3.9.
|
2014-02-21 03:10:09 +00:00
|
|
|
|
|
|
|
|
**Q. Is it possible to remove a patch?**
|
|
|
|
|
|
2014-04-26 04:05:26 +00:00
|
|
|
Yes. Just run `kpatch unload` which will disable and unload the patch module
|
|
|
|
|
and restore the function to its original state.
|
2014-02-21 03:10:09 +00:00
|
|
|
|
|
|
|
|
**Q. Can you apply multiple patches?**
|
|
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
Yes, but to prevent any unexpected interactions between multiple patch modules,
|
2015-11-16 15:38:38 +00:00
|
|
|
it's recommended that patch upgrades are cumulative, so that each patch is a
|
|
|
|
|
superset of the previous patch. This can be achieved by combining the new
|
|
|
|
|
patch with the previous patch using `combinediff` before running
|
|
|
|
|
`kpatch-build`.
|
2014-02-21 03:10:09 +00:00
|
|
|
|
2014-04-23 19:22:58 +00:00
|
|
|
**Q. Why did kpatch-build detect a changed function that wasn't touched by the
|
|
|
|
|
source patch?**
|
|
|
|
|
|
|
|
|
|
There could be a variety of reasons for this, such as:
|
|
|
|
|
|
|
|
|
|
- The patch changed an inline function.
|
|
|
|
|
- The compiler decided to inline a changed function, resulting in the outer
|
|
|
|
|
function getting recompiled. This is common in the case where the inner
|
|
|
|
|
function is static and is only called once.
|
2014-02-21 03:10:09 +00:00
|
|
|
|
2014-10-31 16:45:48 +00:00
|
|
|
**Q. How do I patch a function which is always on the stack of at least one
|
|
|
|
|
task, such as schedule(), sys_poll(), sys_select(), sys_read(),
|
|
|
|
|
sys_nanosleep(), etc?**
|
|
|
|
|
|
|
|
|
|
- If you're sure it would be safe for the old function and the new function to
|
|
|
|
|
run simultaneously, use the `KPATCH_FORCE_UNSAFE` macro to skip the
|
|
|
|
|
activeness safety check for the function. See `kmod/patch/kpatch-macros.h`
|
|
|
|
|
for more details.
|
|
|
|
|
|
|
|
|
|
**Q. Are patching of kernel modules supported?**
|
|
|
|
|
|
|
|
|
|
- Yes.
|
|
|
|
|
|
2015-06-24 21:29:02 +00:00
|
|
|
**Q. Can you patch out-of-tree modules?**
|
|
|
|
|
|
|
|
|
|
- Yes, though it's currently a bit of a manual process. See this
|
|
|
|
|
[message](https://www.redhat.com/archives/kpatch/2015-June/msg00004.html) on
|
|
|
|
|
the kpatch mailing list for more information.
|
|
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
|
2014-02-18 23:33:20 +00:00
|
|
|
Get involved
|
|
|
|
|
------------
|
|
|
|
|
|
2014-04-29 02:13:14 +00:00
|
|
|
If you have questions or feedback, join the #kpatch IRC channel on freenode and
|
|
|
|
|
say hi. We also have a [mailing list](https://www.redhat.com/mailman/listinfo/kpatch).
|
2014-02-18 23:33:20 +00:00
|
|
|
|
2014-03-19 15:29:07 +00:00
|
|
|
Contributions are very welcome. Feel free to open issues or PRs on github.
|
|
|
|
|
For big PRs, it's a good idea to discuss them first in github issues or on the
|
|
|
|
|
[mailing list](https://www.redhat.com/mailman/listinfo/kpatch) before you write
|
|
|
|
|
a lot of code.
|
2014-02-18 23:33:20 +00:00
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
License
|
|
|
|
|
-------
|
|
|
|
|
|
|
|
|
|
kpatch is under the GPLv2 license.
|
|
|
|
|
|
|
|
|
|
This program is free software; you can redistribute it and/or
|
|
|
|
|
modify it under the terms of the GNU General Public License
|
|
|
|
|
as published by the Free Software Foundation; either version 2
|
|
|
|
|
of the License, or (at your option) any later version.
|
|
|
|
|
|
|
|
|
|
This program is distributed in the hope that it will be useful,
|
|
|
|
|
but WITHOUT ANY WARRANTY; without even the implied warranty of
|
|
|
|
|
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
|
|
|
|
GNU General Public License for more details.
|
|
|
|
|
|
|
|
|
|
You should have received a copy of the GNU General Public License
|
|
|
|
|
along with this program; if not, write to the Free Software
|
|
|
|
|
Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA.
|