2014-02-17 15:54:25 +00:00
|
|
|
kpatch: dynamic kernel patching
|
|
|
|
|
===============================
|
2014-02-11 20:34:19 +00:00
|
|
|
|
2014-05-01 17:15:30 +00:00
|
|
|
kpatch is a Linux dynamic kernel patching infrastructure which allows you to
|
|
|
|
|
patch a running kernel without rebooting or restarting any processes. It
|
|
|
|
|
enables sysadmins to apply critical security patches to the kernel immediately,
|
|
|
|
|
without having to wait for long-running tasks to complete, for users to log
|
|
|
|
|
off, or for scheduled reboot windows. It gives more control over uptime
|
|
|
|
|
without sacrificing security or stability.
|
2014-02-11 20:34:19 +00:00
|
|
|
|
2014-02-18 23:33:20 +00:00
|
|
|
**WARNING: Use with caution! Kernel crashes, spontaneous reboots, and data loss
|
|
|
|
|
may occur!**
|
|
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
Here's a video of kpatch in action:
|
|
|
|
|
|
2017-10-12 15:32:12 +00:00
|
|
|
[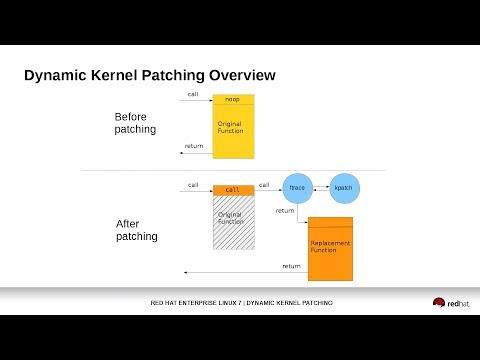](https://www.youtube.com/watch?v=juyQ5TsJRTA)
|
2014-06-18 19:41:31 +00:00
|
|
|
|
2014-07-11 14:53:23 +00:00
|
|
|
And a few more:
|
|
|
|
|
|
|
|
|
|
- https://www.youtube.com/watch?v=rN0sFjrJQfU
|
|
|
|
|
- https://www.youtube.com/watch?v=Mftc80KyjA4
|
|
|
|
|
|
2020-05-08 16:19:06 +00:00
|
|
|
Table of contents
|
|
|
|
|
=================
|
|
|
|
|
|
2020-05-12 02:19:25 +00:00
|
|
|
- [Supported Architectures](#supported-architectures)
|
2020-05-08 16:19:06 +00:00
|
|
|
- [Installation](#installation)
|
|
|
|
|
- [Quick start](#quick-start)
|
|
|
|
|
- [Patch Author Guide](#patch-author-guide)
|
|
|
|
|
- [How it works](#how-it-works)
|
|
|
|
|
- [kpatch-build](#kpatch-build)
|
|
|
|
|
- [Limitations](#limitations)
|
|
|
|
|
- [Frequently Asked Questions](#frequently-asked-questions)
|
|
|
|
|
- [Get involved](#get-involved)
|
|
|
|
|
- [License](#license)
|
|
|
|
|
|
2020-05-12 02:19:25 +00:00
|
|
|
|
|
|
|
|
Supported Architectures
|
|
|
|
|
-----------------------
|
|
|
|
|
|
|
|
|
|
- [x] x86-64
|
|
|
|
|
- [x] ppc64le
|
|
|
|
|
- [ ] arm64
|
2022-03-29 08:21:26 +00:00
|
|
|
- [x] s390 [upstream prerequisites](doc/s390-upstream-prerequisites.md)
|
2020-05-12 02:19:25 +00:00
|
|
|
|
2014-02-17 15:54:25 +00:00
|
|
|
Installation
|
|
|
|
|
------------
|
2014-02-13 16:04:35 +00:00
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
See [INSTALL.md](doc/INSTALL.md).
|
2014-04-22 02:43:57 +00:00
|
|
|
|
2014-02-13 16:04:35 +00:00
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
Quick start
|
2014-02-17 15:54:25 +00:00
|
|
|
-----------
|
2014-02-13 03:53:05 +00:00
|
|
|
|
2014-07-30 10:08:17 +00:00
|
|
|
> NOTE: While kpatch is designed to work with any recent Linux
|
2022-04-22 16:25:02 +00:00
|
|
|
kernel on any distribution, `kpatch-build` has specifically been tested and
|
|
|
|
|
confirmed to work on Fedora and RHEL. It has also been known to work on Oracle
|
|
|
|
|
Linux, Ubuntu, Debian, and Gentoo.
|
2014-02-13 03:53:05 +00:00
|
|
|
|
2014-05-02 22:28:58 +00:00
|
|
|
First, make a source code patch against the kernel tree using diff, git, or
|
|
|
|
|
quilt.
|
|
|
|
|
|
|
|
|
|
As a contrived example, let's patch /proc/meminfo to show VmallocChunk in ALL
|
|
|
|
|
CAPS so we can see it better:
|
|
|
|
|
|
|
|
|
|
$ cat meminfo-string.patch
|
|
|
|
|
Index: src/fs/proc/meminfo.c
|
|
|
|
|
===================================================================
|
|
|
|
|
--- src.orig/fs/proc/meminfo.c
|
|
|
|
|
+++ src/fs/proc/meminfo.c
|
|
|
|
|
@@ -95,7 +95,7 @@ static int meminfo_proc_show(struct seq_
|
|
|
|
|
"Committed_AS: %8lu kB\n"
|
|
|
|
|
"VmallocTotal: %8lu kB\n"
|
|
|
|
|
"VmallocUsed: %8lu kB\n"
|
|
|
|
|
- "VmallocChunk: %8lu kB\n"
|
|
|
|
|
+ "VMALLOCCHUNK: %8lu kB\n"
|
|
|
|
|
#ifdef CONFIG_MEMORY_FAILURE
|
|
|
|
|
"HardwareCorrupted: %5lu kB\n"
|
|
|
|
|
#endif
|
2014-02-18 04:37:07 +00:00
|
|
|
|
2014-04-01 21:40:28 +00:00
|
|
|
Build the patch module:
|
2014-02-18 04:37:07 +00:00
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
$ kpatch-build meminfo-string.patch
|
2014-05-02 22:28:58 +00:00
|
|
|
Using cache at /home/jpoimboe/.kpatch/3.13.10-200.fc20.x86_64/src
|
|
|
|
|
Testing patch file
|
|
|
|
|
checking file fs/proc/meminfo.c
|
|
|
|
|
Building original kernel
|
|
|
|
|
Building patched kernel
|
|
|
|
|
Detecting changed objects
|
|
|
|
|
Rebuilding changed objects
|
|
|
|
|
Extracting new and modified ELF sections
|
|
|
|
|
meminfo.o: changed function: meminfo_proc_show
|
2022-04-22 16:25:02 +00:00
|
|
|
Building patch module: livepatch-meminfo-string.ko
|
2014-05-02 22:28:58 +00:00
|
|
|
SUCCESS
|
|
|
|
|
|
|
|
|
|
That outputs a patch module named `kpatch-meminfo-string.ko` in the current
|
2014-02-18 04:37:07 +00:00
|
|
|
directory. Now apply it to the running kernel:
|
|
|
|
|
|
2014-05-02 22:28:58 +00:00
|
|
|
$ sudo kpatch load kpatch-meminfo-string.ko
|
2022-04-22 16:25:02 +00:00
|
|
|
loading patch module: livepatch-meminfo-string.ko
|
2014-02-18 04:37:07 +00:00
|
|
|
|
|
|
|
|
Done! The kernel is now patched.
|
2014-02-13 03:53:05 +00:00
|
|
|
|
2014-05-02 22:28:58 +00:00
|
|
|
$ grep -i chunk /proc/meminfo
|
|
|
|
|
VMALLOCCHUNK: 34359337092 kB
|
2014-02-13 16:04:35 +00:00
|
|
|
|
2015-11-16 20:59:41 +00:00
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
Patch author guide
|
2015-11-16 20:59:41 +00:00
|
|
|
------------------
|
|
|
|
|
|
|
|
|
|
Unfortunately, live patching isn't always as easy as the previous example, and
|
|
|
|
|
can have some major pitfalls if you're not careful. To learn more about how to
|
|
|
|
|
properly create live patches, see the [Patch Author
|
|
|
|
|
Guide](doc/patch-author-guide.md).
|
|
|
|
|
|
2017-10-11 08:08:00 +00:00
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
How it works
|
2014-02-17 15:54:25 +00:00
|
|
|
------------
|
2014-02-11 18:00:17 +00:00
|
|
|
|
2014-02-19 03:32:24 +00:00
|
|
|
kpatch works at a function granularity: old functions are replaced with new
|
2022-04-22 16:25:02 +00:00
|
|
|
ones. It has three main components:
|
2014-02-19 03:32:24 +00:00
|
|
|
|
|
|
|
|
- **kpatch-build**: a collection of tools which convert a source diff patch to
|
2014-04-01 21:40:28 +00:00
|
|
|
a patch module. They work by compiling the kernel both with and without
|
|
|
|
|
the source patch, comparing the binaries, and generating a patch module
|
2014-02-19 03:32:24 +00:00
|
|
|
which includes new binary versions of the functions to be replaced.
|
|
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
- **patch module**: a kernel livepatch module (.ko file) which includes the
|
|
|
|
|
replacement functions and metadata about the original functions. Upon
|
|
|
|
|
loading, it registers itself with the kernel livepatch infrastructure
|
|
|
|
|
(CONFIG\_LIVEPATCH) which does the patching.
|
2014-02-19 03:32:24 +00:00
|
|
|
|
|
|
|
|
- **kpatch utility:** a command-line tool which allows a user to manage a
|
2014-04-01 21:40:28 +00:00
|
|
|
collection of patch modules. One or more patch modules may be
|
2014-02-19 15:50:56 +00:00
|
|
|
configured to load at boot time, so that a system can remain patched
|
2014-02-19 03:32:24 +00:00
|
|
|
even after a reboot into the same version of the kernel.
|
|
|
|
|
|
|
|
|
|
|
2014-03-10 14:24:40 +00:00
|
|
|
### kpatch-build
|
2014-02-11 18:00:17 +00:00
|
|
|
|
2014-04-01 21:40:28 +00:00
|
|
|
The "kpatch-build" command converts a source-level diff patch file to a kernel
|
|
|
|
|
patch module. Most of its work is performed by the kpatch-build script
|
2014-06-16 04:32:08 +00:00
|
|
|
which uses a utility named `create-diff-object` to compare changed objects.
|
2014-02-11 18:00:17 +00:00
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
The primary steps in kpatch-build are:
|
|
|
|
|
- Build the unstripped vmlinux for the kernel
|
|
|
|
|
- Patch the source tree
|
|
|
|
|
- Rebuild vmlinux and monitor which objects are being rebuilt.
|
2014-02-11 18:00:17 +00:00
|
|
|
These are the "changed objects".
|
2014-02-18 16:15:13 +00:00
|
|
|
- Recompile each changed object with `-ffunction-sections -fdata-sections`,
|
2014-02-11 18:00:17 +00:00
|
|
|
resulting in the changed patched objects
|
|
|
|
|
- Unpatch the source tree
|
2014-02-18 16:15:13 +00:00
|
|
|
- Recompile each changed object with `-ffunction-sections -fdata-sections`,
|
2014-02-13 13:49:02 +00:00
|
|
|
resulting in the changed original objects
|
2014-06-16 04:32:08 +00:00
|
|
|
- For every changed object, use `create-diff-object` to do the following:
|
|
|
|
|
* Analyze each original/patched object pair for patchability
|
2014-06-18 19:41:31 +00:00
|
|
|
* Add `.kpatch.funcs` and `.rela.kpatch.funcs` sections to the output object.
|
2014-06-16 04:32:08 +00:00
|
|
|
The kpatch core module uses this to determine the list of functions
|
|
|
|
|
that need to be redirected using ftrace.
|
2014-06-16 04:40:48 +00:00
|
|
|
* Add `.kpatch.dynrelas` and `.rela.kpatch.dynrelas` sections to the output object.
|
2014-06-16 04:32:08 +00:00
|
|
|
This will be used to resolve references to non-included local
|
|
|
|
|
and non-exported global symbols. These relocations will be resolved by the kpatch core module.
|
|
|
|
|
* Generate the resulting output object containing the new and modified sections
|
2014-02-18 16:15:13 +00:00
|
|
|
- Link all the output objects into a cumulative object
|
2014-04-01 21:40:28 +00:00
|
|
|
- Generate the patch module
|
2014-02-11 20:34:19 +00:00
|
|
|
|
2017-10-11 08:08:00 +00:00
|
|
|
|
2014-02-18 23:33:20 +00:00
|
|
|
Limitations
|
|
|
|
|
-----------
|
|
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
- NOTE: Many of these limitations can be worked around with creative solutions.
|
|
|
|
|
For more details, see the [Patch Author Guide](doc/patch-author-guide.md).
|
|
|
|
|
|
2014-03-21 19:57:52 +00:00
|
|
|
- Patches which modify init functions (annotated with `__init`) are not
|
|
|
|
|
supported. kpatch-build will return an error if the patch attempts
|
|
|
|
|
to do so.
|
|
|
|
|
|
2018-10-21 06:41:35 +00:00
|
|
|
- Patches which modify statically allocated data are not directly supported.
|
|
|
|
|
kpatch-build will detect that and return an error. This limitation can be
|
|
|
|
|
overcome by using callbacks or shadow variables, as described in the
|
|
|
|
|
[Patch Author Guide](doc/patch-author-guide.md).
|
2014-03-21 19:57:52 +00:00
|
|
|
|
|
|
|
|
- Patches which change the way a function interacts with dynamically
|
|
|
|
|
allocated data might be safe, or might not. It isn't possible for
|
|
|
|
|
kpatch-build to verify the safety of this kind of patch. It's up to
|
|
|
|
|
the user to understand what the patch does, whether the new functions
|
|
|
|
|
interact with dynamically allocated data in a different way than the
|
|
|
|
|
old functions did, and whether it would be safe to atomically apply
|
|
|
|
|
such a patch to a running kernel.
|
2014-02-18 23:33:20 +00:00
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
- Patches which modify functions in vdso are not supported. These run in
|
|
|
|
|
user-space and ftrace can't hook them.
|
|
|
|
|
|
2017-03-10 19:06:20 +00:00
|
|
|
- Patches which modify functions that are missing a `fentry` call are not
|
|
|
|
|
supported. This includes any `lib-y` targets that are archived into a
|
|
|
|
|
`lib.a` library for later linking (for example, `lib/string.o`).
|
|
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
- Some incompatibilities currently exist between kpatch and usage of ftrace and
|
|
|
|
|
kprobes. See the Frequently Asked Questions section for more details.
|
|
|
|
|
|
2014-02-18 23:33:20 +00:00
|
|
|
|
2014-02-19 21:49:15 +00:00
|
|
|
Frequently Asked Questions
|
|
|
|
|
--------------------------
|
|
|
|
|
|
|
|
|
|
**Q. Isn't this just a virus/rootkit injection framework?**
|
|
|
|
|
|
|
|
|
|
kpatch uses kernel modules to replace code. It requires the `CAP_SYS_MODULE`
|
|
|
|
|
capability. If you already have that capability, then you already have the
|
|
|
|
|
ability to arbitrarily modify the kernel, with or without kpatch.
|
|
|
|
|
|
|
|
|
|
**Q. How can I detect if somebody has patched the kernel?**
|
|
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
If a patch is currently applied, you can see it in `/sys/kernel/livepatch`.
|
|
|
|
|
|
|
|
|
|
Also, if a patch has been previously applied, the `TAINT_LIVEPATCH` flag is
|
|
|
|
|
set. To test for these flags, `cat /proc/sys/kernel/tainted` and check to see
|
|
|
|
|
if the value of `TAINT_LIVEPATCH` (32768) has been OR'ed in.
|
2014-05-01 17:15:58 +00:00
|
|
|
|
2014-05-01 17:19:41 +00:00
|
|
|
Note that the `TAINT_OOT_MODULE` flag (4096) will also be set, since the patch
|
2014-05-01 17:15:58 +00:00
|
|
|
module is built outside the Linux kernel source tree.
|
|
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
If your patch module is unsigned, the `TAINT_UNSIGNED_MODULE` flag (8192) will
|
|
|
|
|
also be set.
|
2017-02-06 18:51:53 +00:00
|
|
|
|
2014-02-19 21:49:15 +00:00
|
|
|
**Q. Will it destabilize my system?**
|
|
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
No, as long as the patch is created carefully. See the Limitations section
|
|
|
|
|
above and the [Patch Author Guide](doc/patch-author-guide.md).
|
2014-02-19 21:49:15 +00:00
|
|
|
|
|
|
|
|
**Q. Why not use something like kexec instead?**
|
|
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
If you want to avoid a hardware reboot, but are ok with restarting processes or
|
|
|
|
|
using CRIU, kexec is a good alternative.
|
2014-02-19 21:49:15 +00:00
|
|
|
|
|
|
|
|
**Q. If an application can't handle a reboot, it's designed wrong.**
|
|
|
|
|
|
|
|
|
|
That's a good poi... [system reboots]
|
|
|
|
|
|
2014-02-21 03:10:09 +00:00
|
|
|
**Q. What kernels are supported?**
|
|
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
kpatch needs gcc >= 4.8 and Linux >= 4.0.
|
2014-02-21 03:10:09 +00:00
|
|
|
|
|
|
|
|
**Q. Is it possible to remove a patch?**
|
|
|
|
|
|
2014-04-26 04:05:26 +00:00
|
|
|
Yes. Just run `kpatch unload` which will disable and unload the patch module
|
|
|
|
|
and restore the function to its original state.
|
2014-02-21 03:10:09 +00:00
|
|
|
|
|
|
|
|
**Q. Can you apply multiple patches?**
|
|
|
|
|
|
2014-06-18 19:41:31 +00:00
|
|
|
Yes, but to prevent any unexpected interactions between multiple patch modules,
|
2015-11-16 15:38:38 +00:00
|
|
|
it's recommended that patch upgrades are cumulative, so that each patch is a
|
|
|
|
|
superset of the previous patch. This can be achieved by combining the new
|
|
|
|
|
patch with the previous patch using `combinediff` before running
|
2022-04-22 16:25:02 +00:00
|
|
|
`kpatch-build`. It's also recommended to use livepatch atomic "replace" mode,
|
|
|
|
|
which is the default.
|
2014-02-21 03:10:09 +00:00
|
|
|
|
2014-04-23 19:22:58 +00:00
|
|
|
**Q. Why did kpatch-build detect a changed function that wasn't touched by the
|
|
|
|
|
source patch?**
|
|
|
|
|
|
|
|
|
|
There could be a variety of reasons for this, such as:
|
|
|
|
|
|
|
|
|
|
- The patch changed an inline function.
|
|
|
|
|
- The compiler decided to inline a changed function, resulting in the outer
|
|
|
|
|
function getting recompiled. This is common in the case where the inner
|
|
|
|
|
function is static and is only called once.
|
2022-04-22 16:25:02 +00:00
|
|
|
- A bug in kpatch-build's detection of `__LINE__` macro usage.
|
2014-10-31 16:45:48 +00:00
|
|
|
|
|
|
|
|
**Q. Are patching of kernel modules supported?**
|
|
|
|
|
|
|
|
|
|
- Yes.
|
|
|
|
|
|
2015-06-24 21:29:02 +00:00
|
|
|
**Q. Can you patch out-of-tree modules?**
|
|
|
|
|
|
2018-10-23 21:25:19 +00:00
|
|
|
Yes! There's a few requirements, and the feature is still in its infancy.
|
|
|
|
|
|
2019-02-14 19:59:59 +00:00
|
|
|
1. You need to use the `--oot-module` flag to specify the version of the
|
2018-10-23 21:25:19 +00:00
|
|
|
module that's currently running on the machine.
|
2021-12-06 14:02:04 +00:00
|
|
|
2. `--oot-module-src` has to be passed with a directory containing the same
|
2018-10-23 21:25:19 +00:00
|
|
|
version of code as the running module, all set up and ready to build with a
|
|
|
|
|
`make` command. For example, some modules need `autogen.sh` and
|
|
|
|
|
`./configure` to have been run with the appropriate flags to match the
|
|
|
|
|
currently-running module.
|
|
|
|
|
3. If the `Module.symvers` file for the out-of-tree module doesn't appear
|
|
|
|
|
in the root of the provided source directory, a symlink needs to be created
|
|
|
|
|
in that directory that points to its actual location.
|
2019-02-14 19:59:59 +00:00
|
|
|
4. Usually you'll need to pass the `--target` flag as well, to specify the
|
|
|
|
|
proper `make` target names.
|
2018-10-23 21:25:19 +00:00
|
|
|
5. This has only been tested for a single out-of-tree module per patch, and
|
|
|
|
|
not for out-of-tree modules with dependencies on other out-of-tree modules
|
|
|
|
|
built separately.
|
|
|
|
|
|
|
|
|
|
***Sample invocation***
|
|
|
|
|
|
2021-12-06 14:02:04 +00:00
|
|
|
`kpatch-build --oot-module-src ~/test/ --target default --oot-module /lib/modules/$(uname -r)/extra/test.ko test.patch`
|
2015-06-24 21:29:02 +00:00
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
|
2022-09-01 19:43:33 +00:00
|
|
|
**Q. What is needed to support a new architecture?**
|
|
|
|
|
|
|
|
|
|
Porting an architecture can be done in three phases:
|
|
|
|
|
|
|
|
|
|
1. In the kernel, add `CONFIG_HAVE_LIVEPATCH` support. For some arches
|
|
|
|
|
this might be as simple as enabling `CONFIG_DYNAMIC_FTRACE_WITH REGS`.
|
|
|
|
|
With this support you can do basic live patches like those in
|
|
|
|
|
samples/livepatch. Livepatch functionality is limited and extra care
|
|
|
|
|
must be taken to avoid certain pitfalls.
|
|
|
|
|
2. Add kpatch-build (create-diff-object) support. This makes it easier
|
|
|
|
|
to build patches, and avoids some of the pitfalls. For example,
|
|
|
|
|
https://github.com/dynup/kpatch/pull/1203 added s390x support.
|
|
|
|
|
3. Add `CONFIG_HAVE_RELIABLE_STACKTRACE` and (if needed) objtool
|
|
|
|
|
support in the kernel. This avoids more pitfalls and enables full
|
|
|
|
|
livepatch functionality.
|
|
|
|
|
|
|
|
|
|
|
2014-02-18 23:33:20 +00:00
|
|
|
Get involved
|
|
|
|
|
------------
|
|
|
|
|
|
2022-04-22 16:25:02 +00:00
|
|
|
If you have questions or feedback, join the #kpatch IRC channel on
|
|
|
|
|
[Libera](https://libera.chat) and say hi.
|
2014-02-18 23:33:20 +00:00
|
|
|
|
2014-03-19 15:29:07 +00:00
|
|
|
Contributions are very welcome. Feel free to open issues or PRs on github.
|
2022-04-22 16:25:02 +00:00
|
|
|
For big PRs, it's a good idea to discuss them first in github
|
|
|
|
|
issues/discussions or on IRC before you write a lot of code.
|
2014-02-18 23:33:20 +00:00
|
|
|
|
2017-10-11 08:08:00 +00:00
|
|
|
|
2014-02-18 16:15:13 +00:00
|
|
|
License
|
|
|
|
|
-------
|
|
|
|
|
|
|
|
|
|
kpatch is under the GPLv2 license.
|
|
|
|
|
|
|
|
|
|
This program is free software; you can redistribute it and/or
|
|
|
|
|
modify it under the terms of the GNU General Public License
|
|
|
|
|
as published by the Free Software Foundation; either version 2
|
|
|
|
|
of the License, or (at your option) any later version.
|
|
|
|
|
|
|
|
|
|
This program is distributed in the hope that it will be useful,
|
|
|
|
|
but WITHOUT ANY WARRANTY; without even the implied warranty of
|
|
|
|
|
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
|
|
|
|
GNU General Public License for more details.
|
|
|
|
|
|
|
|
|
|
You should have received a copy of the GNU General Public License
|
|
|
|
|
along with this program; if not, write to the Free Software
|
|
|
|
|
Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA.
|